Getty Images
In a growth safety execs feared, attackers are actively concentrating on one more set of essential server vulnerabilities that depart firms and governments open to severe community intrusions.
The vulnerability this time is in BIG-IP, a line of server home equipment offered by Seattle-based F5 Networks. Customers use BIG-IP servers to handle visitors going into and out of massive networks. Tasks embody load balancing, DDoS mitigation, and net software safety.
Last week, F5 disclosed and patched critical BIG-IP vulnerabilities that enable hackers to realize full management of a server. Despite a severity ranking of 9.8 out of 10, the safety flaws acquired overshadowed by a completely different set of essential vulnerabilities Microsoft disclosed and patched in Exchange server a week earlier. Within a few days of Microsoft’s emergency replace, tens of thousands of Exchange servers within the US have been compromised.
Day of reckoning
When safety researchers weren’t busy attending to the unfolding Exchange mass compromise, many of them warned that it was solely a matter of time earlier than the F5 vulnerabilities additionally got here below assault. Now, that day has come.
Researchers at safety agency NCC Group on Friday said they’re “seeing full chain exploitation” of CVE-2021-22986, a vulnerability that enables distant attackers with no password or different credentials to execute instructions of their selection on susceptible BIG-IP units.
“After seeing lots of broken exploits and failed attempts, we are now seeing successful in the wild exploitation of this vulnerability, as of this morning,” Rich Warren, an NCC Group researcher wrote.
After seeing tons of damaged exploits and failed makes an attempt, we are now seeing profitable within the wild exploitation of this vulnerability, as of this morning https://t.co/Sqf55OFkzI
— Rich Warren (@buffaloverflow) March 19, 2021
In a blog post NCC Group posted a screenshot displaying exploit code that might efficiently steal an authenticated session token, which is a kind of browser cookie that enables directors to make use of a web-based programming interface to remotely management BIG-IP {hardware}.
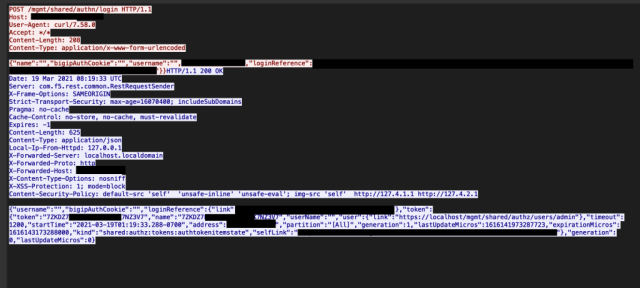
NCC Group
Security agency Palo Alto Networks, in the meantime, said that CVE-2021-22986 was being focused by a units contaminated with a variant of the open-source Mirai malware. The tweet stated the variant was “attempting to exploit” the vulnerability, however it wasn’t clear if the makes an attempt have been profitable.
Other researchers reported Internet-wide scans designed to find BIG-IP servers that are susceptible.
Opportunistic mass scanning exercise detected from the next hosts checking for F5 iControl REST endpoints susceptible to distant command execution (CVE-2021-22986).
112.97.56.78 (????????)
13.70.46.69 (????????)
115.236.5.58 (????????)Vendor advisory: https://t.co/MsZmXEtcTn #threatintel
— Bad Packets (@bad_packets) March 19, 2021
CVE-2021-22986 is just one of a number of essential BIG-IP vulnerabilities F5 disclosed and patched final week. The severity In half is as a result of the vulnerabilities require restricted talent to use. But extra importantly, as soon as attackers have management of a BIG-IP server, they are roughly contained in the safety perimeter of the community utilizing it. That means attackers can shortly entry different delicate elements of the community.
As if admins didn’t have already got sufficient to take care of, patching susceptible BIG-IP servers and in search of exploits must be a prime precedence. NCC Group supplied indicators of compromise within the hyperlink above, and Palo Alto Networks has IOCs here.
